Identity Federation in AWS has been launched since 2011. How AWS’s IAM service changes and grows with market needs?
This article introduces you the backbone of AWS, IAM and its integration with AWS Amplify on the mobile and server-less website. AWS Amplify, with aid from Cognito service, has become a powerful one-stop solution for development and publishing, giving full power and easy integration to the AWS ecosystem.

IAM
AWS Identity and Access Management (IAM) provides easy access control to our AWS account and other AWS resources.
For example, thanks to the fine-grained identity and access management, with access key of an IAM role given permission of programmatic access to the specific s3 bucket, an EC2 instance can access the private s3 bucker. However, the use of access key has some drawbacks, one of which is the inflexibility and access key that is stored in a block is never secure.
IAM with Identity Federation: Providing Access to Externally Authenticated Users
IAM with Identity Federation has been available since 2011, it allows existing identities (e.g. users) in your enterprise to access AWS APIs and resources using IAM’s fine-grained access controls, without the need to create an IAM user for each identity.
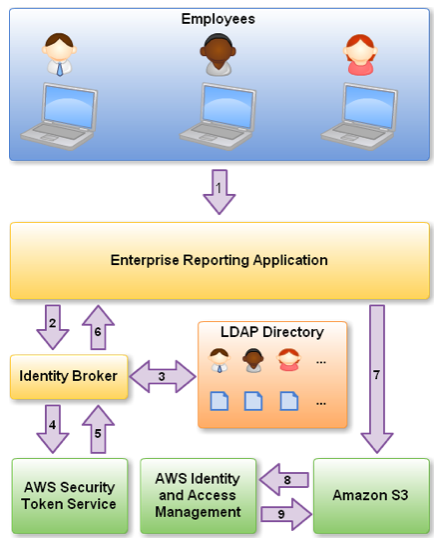
See more: AWS Identity and Access Management – Now With Identity Federation
An Identity Broker can use the organization’s LDAP directory to validate the employee’s identity. This process is called identity federation. The Identity Broker then calls the Security Token Service using IAM credentials, so that the Service provides us with new tokens and other security metrics. The permissions associated with temporary security credentials are at most equal to those of the IAM user who issued them.
As you may have known, when you use an Identity provider (IdP) in the process of identity federation, you don't have to create custom sign-in code or manage your own user identities; the IdP provides that for you. Your external users sign in through a well-known identity provider, such as Login with Amazon, Facebook, Google, and many others.
But the challenge back in that time was that we have to implement the identity broker ourselves. We can create an identity broker with service like KeyCloak. Keycloak is an open source Identity and Access Management. It provides functions on single-sign, Identity Brokering, and Social Login.

Key Cloak as the Identity broker
Yet, Setting up User Federation from identity provider with an identity broker is not easy. So there is a need for the uprise of AWS Cognito. Below are some illustrations provide by AWS:
AWS Cognito
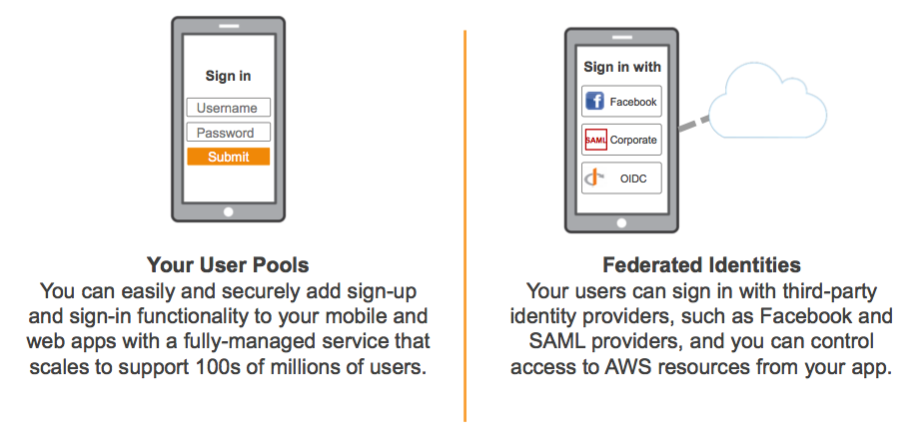
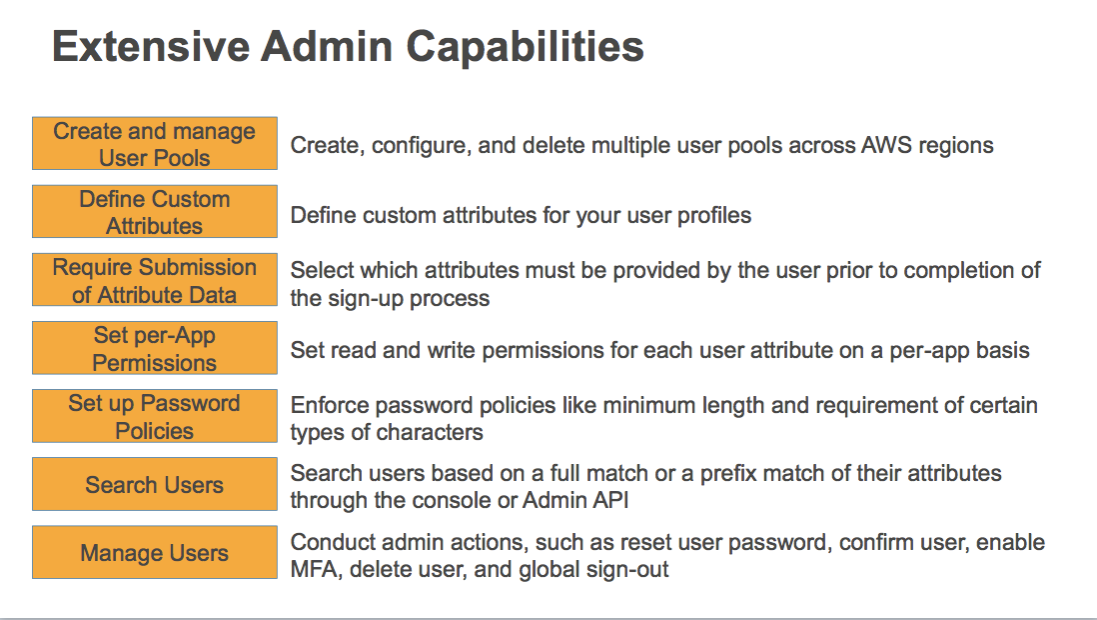
Simply Speaking, Cognito is an implementation of Keycloak Service with addition of User Pool. We can easily manage user in the GUI. Cognito also provides extensive capabilities listed below:


AWS Amplify
AWS Amplify is AWS’s likewise to Google’s Firebase Console. an AWS's Open Source library for developers looking to build cloud-connected applications with JavaScript on the web or mobile platforms.
As it is stated in the documentation, AWS Amplify is designed to give a declarative interface to client developers looking to perform common actions using cloud services in a scalable and secure manner. These new capabilities allow developers writing JavaScript applications to programmatically apply best practices with common abstractions, ultimately resulting in faster development cycles. A comprehensive CLI experience which is fully integrated with AWS Mobile Hub is also available for building applications from scratch or enhancing existing projects with features for the AWS cloud.
The AWS Amplify library modules are broken down into categories (Auth, Analytics, Storage, APIs, Caching) to quickly add features such as User SignUp/SignIn, MFA, tracking or metric analytics, content management or Serverless API integration. The library also has internationalization and localization for multi-language support, as well as caching capabilities. Finally, there are components and extensions for React and React Native, allowing developers writing applications on those platforms to add these capabilities with framework specific standards. JavaScript developers can also use the library to build their own custom UI components, such as custom authentication flows. AWS Amplify is designed to be extended with different implementations among community and partner contributors.
Development Details: Sign In with AWS Amplify
Configuration is easy.
The amplify configure command helps us to build the serverless backend environment in AWS. However, it may have provided too many functions and cumbersomeness to our app and cloud setup, especially when we only want to utilize the authentication function only.
Indeed, looking closely at the logs, we can find out that the CLI setup a Cloud Formation on our AWS with IAM Roles and Bucket policy auto-generated for the other may-not-be-necessary services.
The Amplify is initialized at the entry point of the web app with the configuration settings. To only use the authentication function, only define the setting related to the funcitonality:
import { Auth } from 'aws-amplify';
Auth.signIn(username, password)
.then(user => console.log(user))
.catch(err => console.log(err));
One important but rarely be advised things to note is that there are various kinds of authentication challenges, which is built in for Cognito service for the sake of security. We could have some workarounds, to skip or to auto-complete the challenges. More can be discussed in later blog posts.
cognitoUser.completeNewPasswordChallenge(newPassword, data, {
onSuccess: function(result) {},
onFailure: function(error) {
console.error(error.message)
}
})










Leave a Reply